Supply chain attack postmortem: lessons learnt

A new attack recently surfaced in the DeFi space, this time a sophisticated supply chain attack targeting both developers and users. In this post, we explain what we learnt from the attack and how we are making sure it won’t happen again.
On October 30, 1inch encountered a security incident involving a widely used third-party UI animations library, @lottiefiles/lottie-player, which was compromised, leading to significant risks for applications and wallets interacting with it.
This breach affected certain users’ wallets through a sophisticated method, which has since been fully mitigated by the 1inch team. Importantly, 1inch’s protocols, wallet, and API were not affected.
The attack was identified at 2:31pm PDT. The 1inch team took immediate actions to neutralize the threat and fully resolved the issue by 3:22 PDT.
The anatomy of the attack
The attacker managed to compromise @lottiefiles/lottie-player, a widely-used UI animations library. This incident shows possible risks of using widely adopted software packages, which can pose serious threats when compromised.
The 1inch team believes that the attacker gained access to the library by exploiting compromised secrets from one of the library’s contributors. Once inside, the attacker injected malicious code into the library's updates. This change allowed the library to display a seemingly safe popup requesting a wallet connection, while malicious code was silently running in the background. Once a wallet was connected, the attacker selectively requested extensive permissions to transfer tokens from the address - leading to a partial compromise either immediately or with a delay.
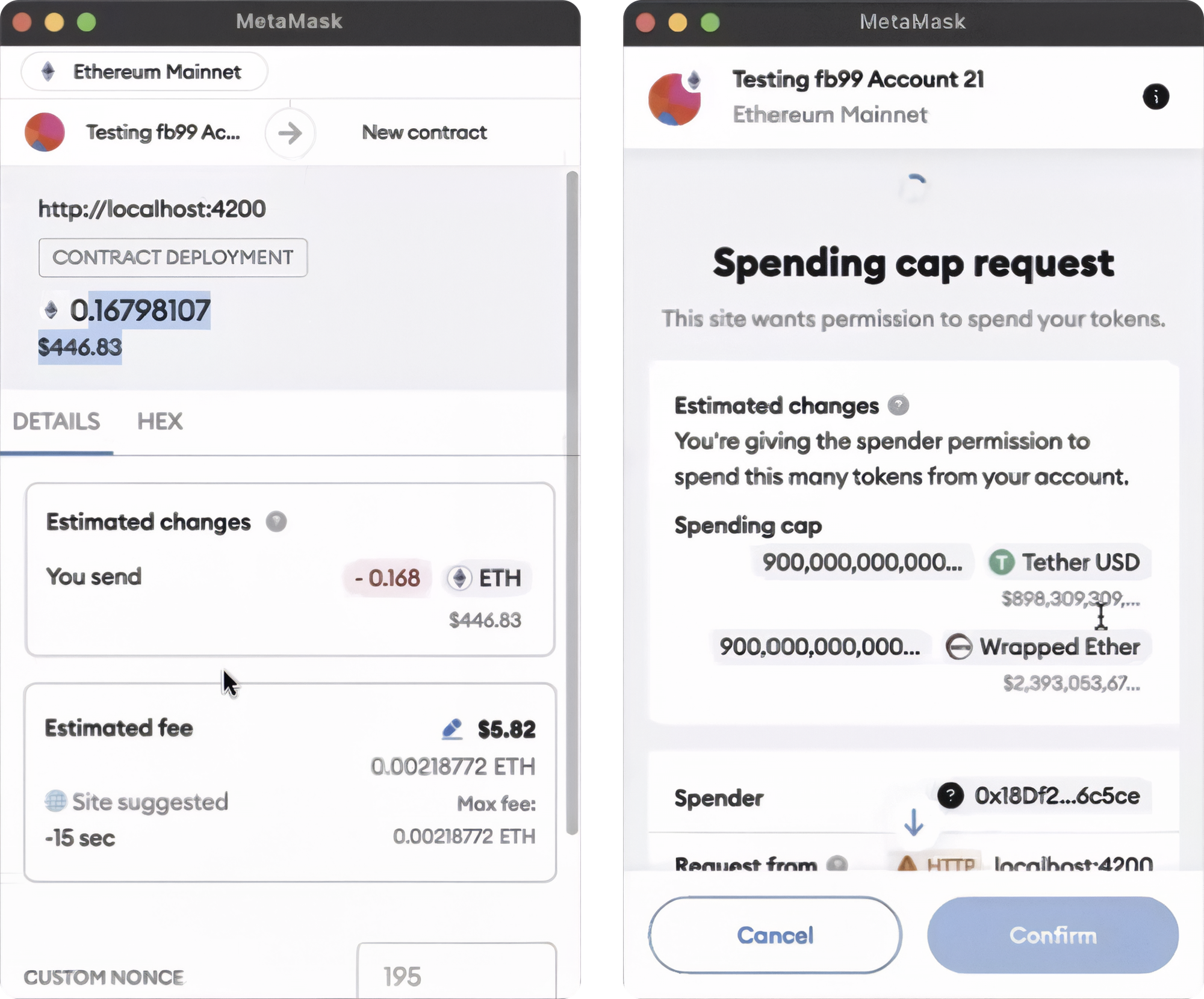
The moment these permissions were granted, the tokens stored in the affected wallets became vulnerable and were often drained without the user's knowledge. It is crucial for everyone in the DeFi community-developers and users alike-to take this incident as a lesson in the hidden dangers of supply chain vulnerabilities.
How 1inch was affected and what the response was
1inch used lottie-player by referencing it through an external URL, meaning the library was loaded directly from an external server instead of being hosted locally within the 1inch infrastructure.
It’s important to note that only the 1inch dApp was affected by this incident. Other products, such as the 1inch Wallet, all the protocols and APIs, remained entirely unaffected.
The compromised library was swiftly identified thanks to @pcaversaccio, who alerted the 1inch team about the issue. Immediately after receiving this information, a group of experts within 1inch was assembled to investigate and mitigate the threat.
During the investigation, the 1inch team discovered that the compromised version of the library had been used. In response, 1inch acted swiftly to roll back to a verified safe version, ensuring the malicious code was completely removed from the 1inch dApp.
Furthermore, the attacker’s drainer account was identified shortly after the incident. This identification helped verify real victims and assess the extent of the losses suffered by those affected.
Security measures and recommendations
Supply chain attacks like this one are a sobering reminder of how deeply dependent the DeFi community is on external software libraries and packages. Let's dive into some practical steps to reduce the risk.
1. Be cautious with wallet permissions
The lottie-player attack used a clever strategy: a popup requesting wallet permissions. In DeFi, such requests are common, but they shouldn't be taken lightly. It’s good practice to always verify which dApp is asking for permissions and who the spender is.
Also, it’s advisable not to give broad permissions unless absolutely necessary, and keep an eye on permission prompts that appear out of context. Tools like Pocket Universe and Wallet Guard can help identify potential risks before you confirm a transaction. Being careful with permissions can often mean the difference between maintaining control of your assets and losing them.
2. Audit and revoke permissions regularly
It's possible that wallets affected by this attack have not yet been drained, as there could be a delay. If you have interacted with a compromised library or have any doubts, act now. Use services like Revoke.cash to audit your permissions. Revoke unnecessary or suspicious approvals to stay ahead of potential attackers.
Consider setting up a schedule to regularly check wallet permissions, especially for wallets that have interacted with multiple dApps and libraries. This proactive approach can significantly reduce risks.
3. Don’t use @latest in production code
It might be tempting to point a dependency to @latest to ensure the most recent version is being used. However, this relinquishes control over what exactly is being deployed in an application. The malicious code injected into @lottiefiles/lottie-player was present in a new release. Automatic updates pulled in the infected version unknowingly.
Instead, explicitly declare your version of the dependencies and audit each update before integrating them into your application. The goal is to ensure that you know exactly what’s being used and have the opportunity to verify each change.
4. Properly manage dependencies
One thing to avoid is blindly trusting any library, no matter how popular. Always do your own research, especially when adopting new updates or dependencies. When feasible, use tools to monitor the integrity of your dependencies and track changes across versions.
Dependency management tools like npm audit or yarn audit can help detect vulnerabilities, but a human review is still necessary. Take the time to check contributors and recent changes, especially for libraries that have broad access to your application’s functionality.
Stay vigilant, stay safe
The recent attack on @lottiefiles/lottie-player highlights a significant vulnerability for DeFi users and developers. 1inch continues to remain committed to further strengthening dependency monitoring and implementing additional safeguards to mitigate future risks. This incident underscores the importance of vigilance in third-party dependency management. 1inch keeps working diligently to enhance the ecosystem’s security practices and remains vigilant about possible future incidents.
The DeFi world is full of opportunities, but it also comes with unique risks. We highly recommend that you stay informed, verify before trusting and always remember that your vigilance is the best defense against threats.
If you have experienced losses related to this issue, reach out to us at https://help.1inch.io for help!




























