A vulnerability disclosed in Profanity, an Ethereum vanity address tool

This post explains an apparent hack of the Ethereum vanity address generating tool Profanity, uncovered by 1inch contributors.
Notice: Your money is NOT SAFU if your wallet address was generated with the Profanity tool. Transfer all of your assets to a different wallet ASAP! Moreover, if you used Profanity to get a vanity smart contract address, make sure to change the owners of that smart contract. Meanwhile, the ERADICATE tool from the same creator doesn’t appear to have the vulnerability described in this post.
Ethereum users generate wallets by computing a hash of a public key derived from a random private key. These addresses usually look randomized, but the more addresses you generate, the higher chances are that you could find any prefix, suffix or middle part. There are tools allowing users to generate millions of addresses per second. One of the most popular and highly efficient of them is Profanity.
In early 2022, some of the 1inch contributors noticed that Profanity used a random 32-bit vector to seed 256-bit private keys and suspected it could be unsafe.
This is how Profanity works:
- Randomly select 1 of 4 bln seed private keys.
- Expand it deterministically to 2 mln private keys.
- Derive public keys from these private keys.
- Repeatedly increment them until they reach the desired vanity address.
Initially, the 1inch contributors thought it was possible to recompute all the vanity addresses by reseeding all 4 bln initial vectors. It would have required thousands of GPUs and months of time to recalculate all the 6–7 character vanity addresses. At first sight, it appeared that 8+ character vanity addresses were quite safe (please, read through the end of this post).
In June 2022, a 1inch contributor received a strange message from @samczsun regarding suspicious activity of one of the 1inch deployer wallets, as well as Synthetix’ and some others:
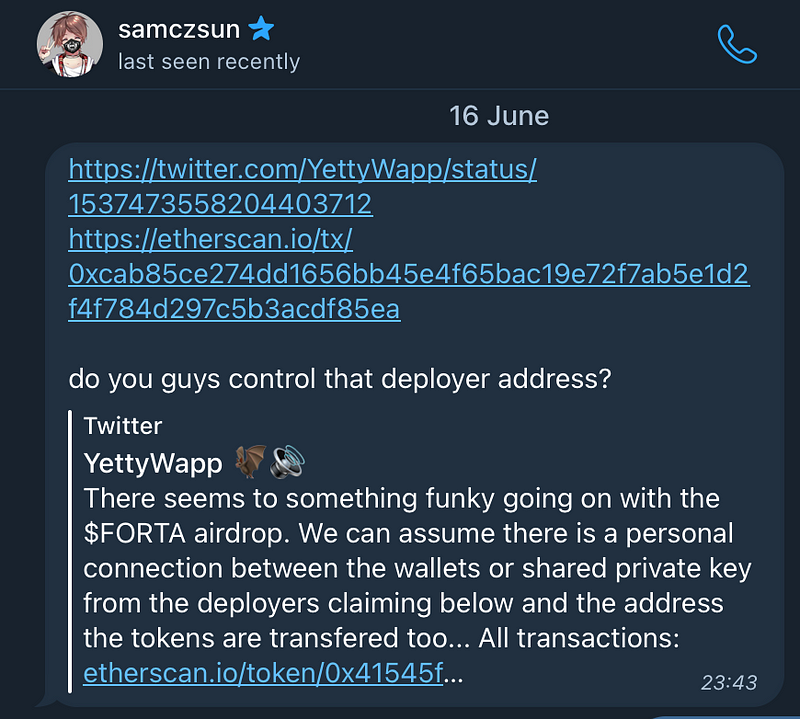
At least 5 deployers of different projects claimed the same airdrop:
https://twitter.com/YettyWapp/status/1537473558204403712
Subsequently, the claimed funds were transferred to a single wallet:
https://etherscan.io/address/0xee9bd0e71681ee6e9aa9f1ba46d2d1149f7bd054
That was getting really suspicious. As there were signs that a hack must have taken place, 1inch contributors spent some time investigating and, a few weeks ago, realized that vanity address brute force could be turned back to original 4 bln of seeds in a more efficient manner:
- Get a public key from a vanity address (recover from the transaction signature).
- Expand it deterministically to 2 mln public keys.
- Repeatedly decrement them until they reach the seed public key.
A few days ago, the involved 1inch contributors achieved proof-of-concept code allowing them to recover private keys from any vanity address generated with Profanity at almost the same time that was required to generate that vanity address.
The 1inch contributors checked the richest vanity addresses on popular networks and came to the conclusion that most of them were not created by the Profanity tool. But Profanity is one of the most popular tools due to its high efficiency. Sadly, that could only mean that most of the Profanity wallets were secretly hacked.
Meanwhile, the 1inch contributors are still trying to determine all the vanity addresses which were hacked. It’s not a simple task, but at this point it looks like tens of millions of dollars in cryptocurrency could be stolen, if not hundreds of millions. One good thing is that proofs of hacks are available on-chain forever.




























