1inch did the best to help to recover $25M stolen from dForce ecosystem

A hacker who stole the funds from DeFi platform Cryptobonuses.com voluntarily returned the entire amount.
On April 19, the global decentralized finance (DeFi) space suffered a serious blow as a hacker attacked the Chinese lending platform Lendf.me, which is part of dForce ecosystem, and stole roughly $25M, or nearly all of the funds staked on the platform.
The attacker exploited in dForce a vulnerability caused by using the ERC-777 token standard and technique known as reentrancy attack. More here!
Suspicious activity
Soon after the attack occurred, we detected suspicious activity: a user was making multiple exchange transactions, opening our dApp over the content delivery network (CDN) https://app.1inch.io as opposed to the IPFS-based frontend under https://1inch.eth.link.
The same Chinese IP address was appearing before each exchange transaction and we figured it was the cybercriminal who stole funds from dForce.
Luckily, the hacker wasn’t experienced enough, and he left many traces. He was using a VPN or a proxy server rather than a decentralized network, such as Tor. He also left a lot of metadata, and we even knew that he was using a Mac computer and were able to see his screen’s resolution and the system language, which was set to US English.
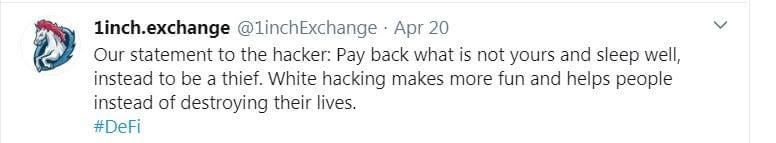
We addressed the hacker in a message on our Twitter account, calling on him to return all the stolen funds.
“Our statement to the hacker: Pay back what is not yours and sleep well, instead to be a thief,” read our address. “White hacking makes more fun and helps people instead of destroying their lives.”
Data sharing issue
Soon after the publication of our tweet, we heard from dForce who requested access to the perpetrator’s IP addresses. But we couldn’t share those.
We have a strict privacy policy which is stated on our website. Protecting our users’ data is vital, and we collect IP addresses only for statistical purposes. Collecting access logs and tracking users with Google Analytics is a common practice across the industry.
If a user doesn’t want to be tracked — no problem, they can use the private mode in their browser or even use Tor network to hide their IP address.
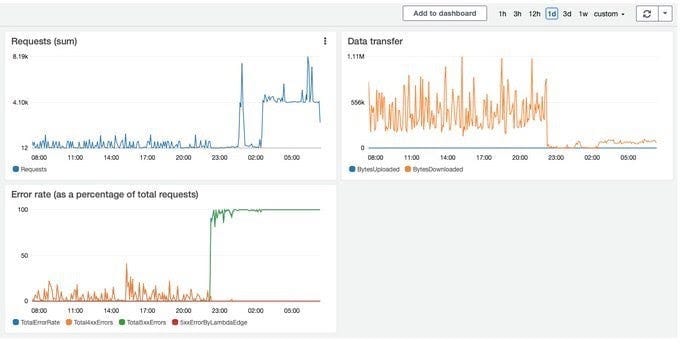
Another reason why we collect user data is to protect ourselves from attacks similar to one that occurred last year, when we were attacked from Canada and California. This is how the attack looked like:
We told dForce that we’d be glad to help out, but they would have to go the official way and contact the police.
Next, the Singapore police force’s criminal investigations department sent us an email, asking for access logs, registration information and any other data that could help locate the hacker.
This was an exceptional case, and we shared the requested data with the police as we believed that would help exercise pressure on the cybercriminal and force him to return the stolen funds.
Happy ending
On April 21, The Block reported that the attacker returned all the stolen funds to Lendf.me. $2.79M was returned on April 20, and the remaining nearly $22M was returned the following day, according to Etherscan data analyzed by The Block.
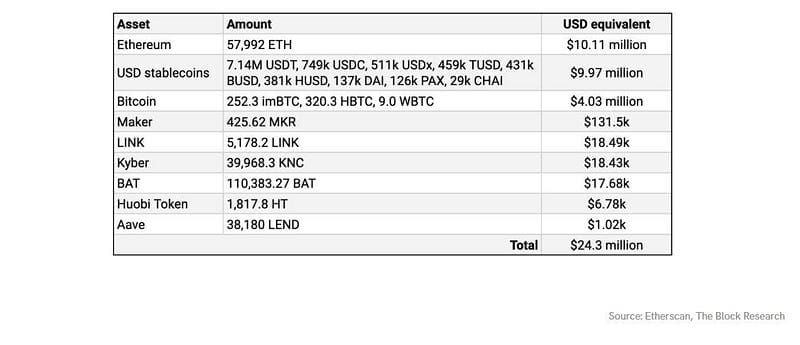
Of course, we don’t have the details but we believe that there were negotiations between dForce and the hacker, and he agreed to voluntarily return the stolen funds under the condition that dForce doesn’t press charges against him.
Well, this story has a happy ending, but it was only possible because the perpetrator turned out to be an inexperienced hacker and left many traces. Otherwise, the ending could have been not so happy.
So, we strongly recommend detailed security audits of smart contracts before releasing any new code to the mainnet. For instance, we recently discovered vulnerability in Fulcrum / bZx which gave us access to $2.5M of user funds. We suggest Red Team Assessment by well known white hackers at least on a quarterly basis.




























